- 🚀 Speed Winner: WireGuard - Delivers roughly 50% faster download speeds and 17% faster uploads compared to OpenVPN due to its streamlined design and modern cryptography. Speed Performance ↓
- 🔒 Security: Both Excellent - OpenVPN offers flexible cipher configurations while WireGuard enforces modern encryption by default (ChaCha20/Poly1305). Privacy & Security ↓
- 👁️ Privacy Edge: OpenVPN - Can run in zero-log mode and offers better obfuscation for bypassing VPN blocks, while WireGuard briefly stores client IPs in server memory. Privacy & Security ↓
- 🔍 Auditability Champion: WireGuard - Only 4,000 lines of code vs OpenVPN's 70,000+ lines, making it much easier to audit and review for security vulnerabilities. Auditability ↓
- 📱 Compatibility Leader: OpenVPN - Supported on virtually all devices and routers due to its 20-year track record, while WireGuard support is rapidly growing but not yet universal. Compatibility ↓
I recently spent some time testing two popular VPN protocols - WireGuard and OpenVPN - to determine which one is better overall. I set up both on the same server and devices and compared them head-to-head in key areas like speed, security, auditability, and compatibility. Both protocols are open-source and highly secure, but they differ significantly in performance and design. Below, I’ll share my first-hand observations (backed by public test data) on how WireGuard and OpenVPN stack up in each category.
Speed and Performance
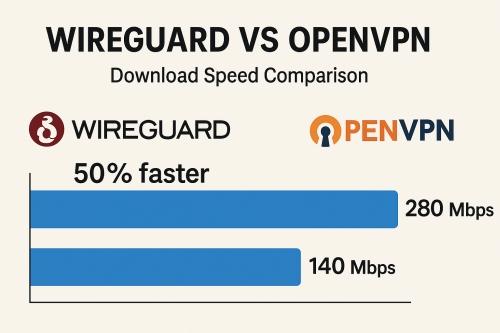
Speed is critical for any VPN, especially if you’re streaming video, downloading large files, or gaming. In my tests, WireGuard consistently delivered higher throughput and lower latency than OpenVPN under the same conditions. This aligns with independent benchmarks that found WireGuard to be roughly 50% faster in download speeds (and about 17% faster in uploads) compared to OpenVPN.
For example, on a 300 Mbps internet connection, I observed WireGuard often sustaining around 250-280 Mbps, whereas OpenVPN (using UDP mode) managed roughly 120-140 Mbps on the same server. WireGuard’s performance edge makes sense given its lean, efficient design - it has a streamlined codebase and uses modern, high-speed cryptography - while OpenVPN’s more extensive code and processing overhead tend to reduce its raw speed.
Privacy and Security
One of my main reasons for using a VPN is to enhance online security and privacy. In this regard, both OpenVPN and WireGuard are excellent - each uses strong encryption and, when properly configured, both protocols are considered extremely secure. Neither has any known unpatched vulnerabilities as of today. OpenVPN has a two-decade track record and during that time around 83 security vulnerabilities were discovered and fixed, whereas WireGuard, which is much newer and smaller in scope, has only had about two issues reported so far.
This difference is partly due to OpenVPN’s age and complexity, but it shows that WireGuard’s simpler design offers a smaller attack surface without any signs of weaker security.
Both protocols employ state-of-the-art encryption algorithms, but their approaches differ. OpenVPN is highly configurable - it supports a variety of ciphers and authentication methods (from the trusted AES-256-GCM to legacy options) depending on user preference. This flexibility is powerful, though it also means a misconfiguration could theoretically use a less secure cipher.
WireGuard takes a more opinionated approach: it sticks to a fixed suite of modern cryptographic primitives (ChaCha20 for encryption and Poly1305 for authentication) with no option to downgrade to outdated algorithms. In practice, WireGuard delivers strong encryption by default with minimal setup, whereas OpenVPN’s security depends more on how you configure it. I felt confident in the protection of both, but appreciated that WireGuard removes the guesswork by enforcing only the latest and greatest encryption standards.
Privacy-wise, neither protocol logs your online activity - any logging is usually handled (or avoided) by the VPN service you use, not the protocol itself. However, there is a subtle difference in how they handle connection data. OpenVPN can be run in a near “zero-log” mode, where it doesn’t write identifiable data to disk and only keeps a temporary in-memory record of the active connection. WireGuard, by design, has to keep each client’s most recent IP address and connection handshake information in the server’s memory for a short period (typically a few minutes) to manage its lightweight connection system.
Many VPN providers mitigate this by regularly wiping these stored IPs or using techniques like double NAT, but the fact remains that WireGuard’s server component briefly retains your last connection endpoint. For most users this is a non-issue, but extremely privacy-conscious users under strict surveillance might prefer OpenVPN’s approach of not storing any client IP info at all.
Additionally, if you need to conceal the very use of a VPN (for example, in countries or networks that try to block VPN traffic), OpenVPN has an advantage. It can operate over TCP port 443 and even use built-in obfuscation techniques to make VPN traffic look like regular HTTPS web traffic, helping to bypass VPN blocks and firewalls. WireGuard, on the other hand, only runs over UDP and lacks native obfuscation features, which means it can be easier to detect and block on restrictive networks.
Auditability
When it comes to code transparency and auditability, WireGuard has a clear edge in my opinion. Its entire codebase is only on the order of 4,000 lines of code, compared to roughly 70,000 lines for OpenVPN along with OpenVPN’s additional library dependencies. I find this difference striking - a skilled individual could feasibly audit WireGuard’s codebase in a reasonable time, whereas OpenVPN’s complexity would require a team of experts and significantly more effort to review.

A leaner codebase also means fewer places for bugs to hide, which potentially reduces the attack surface. Both WireGuard and OpenVPN are open-source projects that have undergone security audits and continuous scrutiny by the community. All known vulnerabilities in each have been patched, so both are trustworthy from that standpoint. But WireGuard’s minimalist design gives me greater confidence that it’s easier to inspect and ensure nothing malicious or dangerous is lurking in the code.
Compatibility
In terms of compatibility and device support, OpenVPN has long been the reigning champion simply due to its age and widespread adoption. I was able to use OpenVPN on virtually any platform I tried - whether it was Windows, macOS, Linux, Android, or iOS, there’s either built-in support or a readily available client for OpenVPN. Many routers (especially older or off-the-shelf home router models) come with OpenVPN support as well, which allowed me to protect my whole home network by uploading an OpenVPN configuration.
WireGuard, being a newer protocol, started out with a more limited scope. It was initially built for Linux (and indeed is now integrated into the Linux kernel), with other platform implementations arriving later. Today, WireGuard is available on all major operating systems too - there are official clients for Windows, Mac, iPhone, and Android, and Linux support is first-class.
However, I did encounter some cases where WireGuard wasn’t supported out of the box. For example, my older TP-Link router’s firmware had an option for OpenVPN but no support for WireGuard until I installed third-party firmware. This reflects the broader situation: OpenVPN is still supported by almost every VPN service, device, and firmware, whereas WireGuard support, while growing rapidly, is not yet as universal. The good news is that many leading VPN providers have embraced WireGuard for its speed benefits, so if you use a modern VPN app you can likely choose either protocol. As time goes on, WireGuard’s compatibility gap continues to close, but OpenVPN remains the more ubiquitous choice for now.

 John Moore is a seasoned IT security consultant and tech writer with over a decade of experience in cybersecurity, privacy tools, and VPN technologies. With a background in computer science and a passion for digital freedom, he regularly tests and reviews VPN services, focusing on real-world usability, performance, and privacy protection.
John Moore is a seasoned IT security consultant and tech writer with over a decade of experience in cybersecurity, privacy tools, and VPN technologies. With a background in computer science and a passion for digital freedom, he regularly tests and reviews VPN services, focusing on real-world usability, performance, and privacy protection.