- What Is a VPN Kill Switch?
- Why You Need a VPN Kill Switch
- How Does a VPN Kill Switch Work?
- Types of VPN Kill Switches
- Comparison of Kill Switch Types
- Application-Level Kill Switch
- System-Level Kill Switch
- Advanced/Persistent Kill Switch
- Implementation and Technical Details
- VPN Services and Kill Switch Features
- Usage Tips and Potential Drawbacks
- Conclusion
A VPN kill switch is a safety feature in VPN (Virtual Private Network) services that protects your privacy by instantly cutting off your internet connection if the VPN connection drops unexpectedly. In essence, it acts as a fail-safe: the moment your secure VPN tunnel goes down, the kill switch kicks in to block all data traffic until the VPN is reconnected. This prevents any of your online activities, IP address, or sensitive data from leaking out on the open internet during that brief lapse. In other words, a kill switch ensures that the worst you experience is a temporary loss of connectivity, rather than a privacy breach.
Why You Need a VPN Kill Switch
Using a VPN without a kill switch is risky because VPN connections aren't infallible - they can drop for many reasons (network issues, weak Wi-Fi, VPN server problems, etc.). Even a momentary drop is enough for your device to revert to the regular, unencrypted internet. That split-second is all it takes for your real IP address and traffic to become visible to websites, your ISP, or attackers. If a kill switch is enabled, however, it immediately halts all internet communication the instant the VPN disconnects, so nothing leaks out.
Privacy and security implications: Without a kill switch, a dropped VPN can expose your IP address, DNS requests, and unencrypted data before you even realize it. This exposure can undo the privacy benefits of the VPN. For example, if you were downloading torrents and your VPN disconnects, your torrent client would broadcast your real IP address to the swarm, potentially leading to copyright notices or legal trouble. Similarly, in countries with censorship or surveillance, if the VPN fails while you're visiting a sensitive website, your activity could be logged by your ISP or observed by authorities. A kill switch prevents these worst-case scenarios by keeping your identity and activity under wraps at all times.
In short, a VPN kill switch isn't an optional luxury - it's often the difference between a clean cutoff of your connection and an instant data leak when something goes wrong. Anyone who relies on a VPN for privacy (be it for file-sharing, evading censorship, or just secure browsing) should consider a kill switch a must-have feature for peace of mind.
How Does a VPN Kill Switch Work?
A VPN kill switch works by continuously monitoring the status of your VPN connection. As long as the encrypted VPN tunnel is active, you can surf normally. The moment the kill switch detects that the VPN connection has failed (due to any dropout or instability), it automatically blocks your device from accessing the internet. Essentially, it isolates you from the web until the secure VPN tunnel is restored, ensuring that no traffic slips outside the encrypted channel.
What happens under the hood? The implementation can vary, but most kill switches use some form of network or firewall control to block traffic:
On desktop systems (Windows, macOS, Linux), the VPN client often adds firewall rules or alters routing tables to allow traffic only via the VPN interface. For example, ExpressVPN's kill switch (Network Lock) inserts a "block everything" firewall rule at the system level, then permits only VPN traffic through. These rules remain in effect during reconnections or network hiccups, covering both IPv4 and IPv6 traffic so no data leaks outside the VPN tunnel.
On mobile devices, kill switches sometimes leverage built-in OS features. Android has an Always-on VPN mode with "Block connections without VPN," which VPN apps can use to ensure no traffic leaves the device unless the VPN is active. iOS similarly can block internet traffic when the VPN disconnects (some apps achieve this via the VPN on-demand settings). In other cases, the VPN app itself monitors the connection and programmatically disables network access when needed.
Once the kill switch has engaged and cut off connectivity, it will typically allow the VPN software to attempt reconnection. As soon as the VPN tunnel is re-established, the kill switch lifts the blockade and normal, protected internet access resumes automatically. This all happens in the background; ideally, you'll just notice that sites stop loading for a moment until the VPN reconnects.
Triggers for activation:
A kill switch may activate due to various VPN disconnection triggers, such as:
Network changes or drops: If you move out of Wi-Fi range or switch networks, the VPN might disconnect, triggering the kill switch.
VPN server issues or congestion: If the server you're connected to goes down or becomes unresponsive, your app may lose the connection.
Software conflicts: Firewall or antivirus software on your device might occasionally interrupt the VPN tunnel.
No matter the cause, the kill switch's job is the same: block all internet traffic until it's safe (i.e., the VPN is back). This protects you from accidental exposure of your IP address, location, or any data that was in transit.
Use-case example: Imagine you're at a café on public Wi-Fi, doing online banking through a VPN. If the Wi-Fi signal drops or the VPN server crashes, a good kill switch will instantly cut your internet access. This means your banking app won't simply reconnect over the unsecured Wi-Fi; instead, it will be offline until the VPN is running again. Without the kill switch, that brief drop could have sent your banking traffic or login details over the open network - a huge security risk. The kill switch essentially locks down your connection during that gap, preserving your privacy.
Types of VPN Kill Switches
Not all VPN kill switches work exactly the same way. Broadly, VPN kill switches come in a couple of flavors, distinguished by their scope of action. The two primary types are application-level and system-level kill switches. Some providers also implement an "advanced" or persistent kill switch, which is an extreme form of system-level protection. We'll explain each type below and compare their pros, cons, and ideal use cases.
Comparison of Kill Switch Types
To summarize the differences between these kill switch types, below is a comparison table outlining their scope, pros, cons, and ideal use-cases:
| Kill Switch Type | Scope of Blocking | Pros | Cons | Ideal Use-Case |
|---|---|---|---|---|
| Application-Level | Blocks specific apps only when VPN drops. You select which programs are cut off, others remain online. | - Fine-grained control: only disconnects chosen sensitive apps. - Minimizes disruption to other internet activities (e.g. music streaming continues). |
- Limited protection: unselected apps can still send data (potential leak). - Requires configuration: user must specify all important apps to protect, which is time-consuming and error-prone. |
Situations where you only need to secure certain activities and want to keep others online. For example, protecting a torrent client, browser, or banking app with the VPN, while allowing less sensitive apps (like a game or Spotify) to stay connected even if VPN drops. |
| System-Level | Blocks all internet traffic on the device if VPN connection fails. (Also called network-level or firewall kill switch.) | - Maximum security: nothing leaks because all connectivity is cut during VPN outages. - One-step setup: just turn it on, no need to configure individual apps. |
- More disruptive: every online task halts until the VPN is back. - Inflexible: you can't exclude specific applications - even harmless traffic is blocked, which might be overkill for some users. |
Scenarios requiring full protection for all apps - e.g. when performing any sensitive browsing, activists/journalists operating in high-censorship regions, or generally for users who prefer security over convenience. Also recommended for torrenting or other P2P activity, to ensure no packet leaks out under your real IP. |
| Persistent (Always-On) | Blocks all internet by default unless VPN is active (even blocks manual disconnects). Often persists through app crashes or device reboot. | - Highest level of protection: absolutely no traffic passes outside the VPN, ever, until you disable the feature. Even rare scenarios (VPN app crash, user forgets to connect) are covered. - Ideal for 24/7 VPN users: you never have to worry about forgetting to turn on the VPN. |
- Most restrictive: you must disable the kill switch or close the app to use the internet without VPN, which can be cumbersome if you temporarily need a direct connection. - May conflict with certain use cases like split tunneling or local network access (since it blocks everything not tunneled). |
Ultra-paranoid or mission-critical privacy use. For example, people who run their entire system behind a VPN at all times (like routing all traffic through a VPN router), or whistleblowers and activists who cannot risk any accidental exposure. Also useful if you often leave your VPN on and want assurance that even on startup or exit, your device won't leak data. |
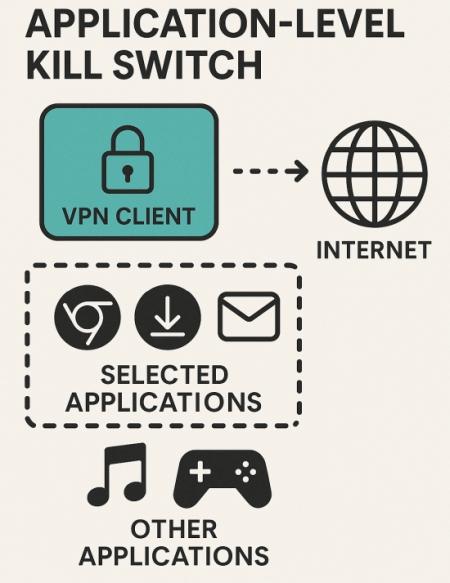
Application-Level Kill Switch
An application-level kill switch (also called a selective kill switch) lets you specify particular applications to protect. If the VPN connection drops, the VPN client will only terminate or block internet access for those chosen apps, while allowing other unrelated apps or background processes to continue using the internet. For example, you might configure an app-level kill switch to cover your web browser, torrent client, and email, but leave streaming music or other non-sensitive apps unaffected.
The upside of this granular approach is more control and less disruption. You can ensure that critical or privacy-sensitive apps are always protected by the VPN, while other activities carry on normally even during a VPN outage. For instance, if your VPN drops while you're watching a video, an app-level kill switch could be set to only pause your browser traffic, but your Spotify or game app might remain online. This flexibility means fewer interruptions to your day-to-day internet usage.
However, the app-level kill switch is less secure than a full-network kill switch. If any application is not covered by the kill switch, that app could still send traffic over the regular internet when the VPN is down. In a worst-case scenario, some background service or unmonitored app might transmit data (revealing your IP or requests) without you realizing it. Therefore, using an application-level kill switch effectively requires that you know which apps handle sensitive info and make sure to include all of them in the protected list. If you forget one (say, a chat application or cloud backup service), that could be a privacy gap. Setting up an app kill switch can also be a bit of work, since you need to configure the list of apps to cover, especially on devices where you use many programs.
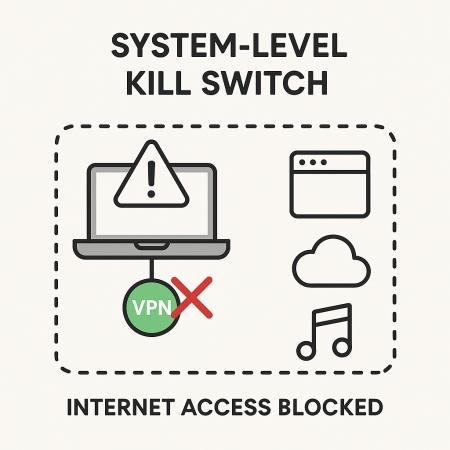
System-Level Kill Switch
A system-level kill switch (also known as a network-level or firewall-level kill switch) is a more blunt but safer tool. Instead of picking and choosing apps, a system-level kill switch will cut off all internet access system-wide if the VPN connection fails. It's an "all-or-nothing" approach: every application and process on the device is blocked from accessing the internet until the VPN is back up. This guarantees that no data can leak outside the encrypted VPN tunnel, because nothing at all is allowed through during the dropout.
The obvious advantage here is maximum security. By shutting down network connectivity entirely, a system-level kill switch eliminates the risk of any accidental data exposure - no app can unknowingly send traffic in the clear. It's also usually easier to use; in most VPN apps, you just toggle the kill switch on, and you're set (no need to specify apps manually). This type is generally considered the more robust and foolproof kill switch, especially for privacy-critical tasks.
The trade-off is convenience. Because it blocks everything, a system-level kill switch will interrupt all your internet-dependent activities when activated. If you were downloading a file, on a video call, or streaming music when the VPN dropped, all of those would halt suddenly. You might not even be able to quickly search for "why is my internet down?" because, from your device's perspective, the internet is "dead" until the VPN reconnects. This can be frustrating, but it's the price for airtight protection. For most privacy-conscious users, the security benefit outweighs the annoyance of reconnecting - it's better to lose the connection for a minute than to accidentally send even a second of unencrypted traffic.
Advanced/Persistent Kill Switch
Some VPN services offer an advanced or persistent kill switch, which is like a supercharged version of the system-level kill switch. In this mode, the VPN application enforces a constant network lock-down by default, allowing no internet traffic at all unless the VPN is actively connected. In practical terms, this means even if you haven't manually started your VPN yet, or if the VPN app crashes, your device still will not send or receive data on the regular internet. The kill switch is effectively "always on," acting as a permanent gatekeeper.
This type of kill switch is extremely uncompromising in protection. It can even survive events like system reboots or app crashes - for example, it might load at startup so that your computer never has a chance to leak data before the VPN launches. Unprotected internet access becomes impossible unless you deliberately turn off the kill switch feature. Mullvad VPN's client is a real-world example: it has an always-on kill switch and a "Lockdown Mode" option that will continue to block internet access even if you click disconnect or quit the VPN app. This ensures that forgetting to connect the VPN after boot, or accidentally closing the app, won't result in any traffic leaking out.
The downside of a persistent kill switch is that it can be inconvenient in certain cases. For instance, if you truly need to access the internet without the VPN (perhaps a specific site blocks VPN IPs, or you're troubleshooting network issues), you must go into settings and turn off the kill switch (or exit the VPN app in a special way) to get connectivity back. Also, features like split tunneling may not work with an always-on kill switch enabled (since by design it blocks non-VPN traffic entirely). But for users who require the highest level of privacy, this trade-off is worth it.
Table Notes: In practice, some VPN providers combine aspects of these types. For instance, a client might offer a system-level kill switch as the default, and an optional app-specific kill switch mode (NordVPN is one such provider). The "persistent" kill switch is usually a mode or setting on top of the system-level kill switch (e.g., Mullvad's "Lockdown Mode" mentioned above) rather than a separate feature - it basically means the kill switch stays enforced even when you intentionally disconnect.
Implementation and Technical Details
From a technical standpoint, a VPN kill switch is typically implemented by manipulating network routing or firewall settings on your device:
Firewall rules approach: Many VPN applications create firewall rules that dynamically block all traffic except via the VPN. For example, enabling the kill switch might add a rule that drops any outgoing connection that is not through the VPN's secure interface. On Windows, this might be done via the Windows Filtering Platform or by disabling the default gateway when the VPN drops; on macOS and Linux, it often uses the built-in packet filter (pf) or iptables to enforce the block. As long as the VPN is connected, an exception rule lets VPN traffic through. If the VPN disconnects, the exception disappears and the firewall rule ensures nothing goes out to the regular internet. When the VPN reconnects, the client re-enables the allowed route for VPN traffic.
Monitoring and network adapters: In addition to firewall rules, some kill switches work by monitoring the VPN process or adapter. If the VPN tunnel goes down, the software can automatically shut down the network adapter or remove the device's default route to the internet, effectively cutting connectivity. This approach is more common in simple or older VPN clients.
OS-level kill switch features: Modern operating systems provide hooks that VPN apps can use. Android's built-in always-on VPN mode is one example - when activated, Android will block any connection that isn't over the VPN. Apps like ExpressVPN or NordVPN tie into this, or instruct users how to enable it in system settings for extra assurance. iOS has a feature called "On Demand VPN" for certain protocols (e.g., IKEv2) which can be configured to not allow traffic outside the VPN as well. VPNs on iOS often implement kill switches internally by leveraging that or by keeping the VPN socket open persistently to prevent leaks.
DNS and IPv6 leaks: A well-implemented kill switch also accounts for different types of traffic. It's important that DNS queries and IPv6 connections are blocked when the VPN drops. Some early or basic kill switches only filtered IPv4 traffic, which could leave an IPv6 leak pathway. Reputable VPNs now block both IPv4 and IPv6 when the kill switch is active, and they often route DNS queries through the VPN as well. This ensures that when your VPN is disconnected, your device isn't silently making DNS requests to your ISP's server or sending IPv6 packets outside.
Limitations and edge cases: While kill switches greatly enhance security, they're not foolproof in every single scenario. For instance, if your computer reboots unexpectedly, there is a short period during startup before the VPN app launches - during that time some applications might attempt to connect to the internet. A persistent kill switch (loading at system boot) can mitigate this, but not all VPNs have that capability. Tests have shown that many VPN kill switches fail to block traffic during system reboot or app crash scenarios. So if you need absolute protection, look for providers that explicitly address this (for example, by running as a service at boot or offering an "always require VPN" mode). Additionally, a kill switch cannot protect you if the VPN connection is active but not actually secure (say, if there's a leak or a misconfiguration) - it only triggers on disconnections, not slow or compromised connections.
VPN Services and Kill Switch Features
Many top-rated VPN services recognize the importance of a kill switch and include it as part of their feature set, though the implementation details can differ:
 NordVPN: NordVPN is known for offering both types of kill switches in its apps. On Windows and some versions of macOS, NordVPN provides an Internet Kill Switch (system-level) that cuts off all traffic, and also an App Kill Switch that lets users specify which applications to shut down if the VPN drops. This gives users flexibility to choose their preferred method. NordVPN's kill switch is available on their desktop and mobile clients (on mobile, it uses the native always-on VPN APIs).
NordVPN: NordVPN is known for offering both types of kill switches in its apps. On Windows and some versions of macOS, NordVPN provides an Internet Kill Switch (system-level) that cuts off all traffic, and also an App Kill Switch that lets users specify which applications to shut down if the VPN drops. This gives users flexibility to choose their preferred method. NordVPN's kill switch is available on their desktop and mobile clients (on mobile, it uses the native always-on VPN APIs).
 Surfshark: Surfshark's apps come with a system-level kill switch that is either on-demand or automatic, but no application-specific kill switch option. In other words, Surfshark will always protect the entire connection if enabled. They support this on Windows, macOS, Android, and iOS. However, notably, Surfshark's Linux client does not currently have a kill switch, which is something to keep in mind for Linux users.
Surfshark: Surfshark's apps come with a system-level kill switch that is either on-demand or automatic, but no application-specific kill switch option. In other words, Surfshark will always protect the entire connection if enabled. They support this on Windows, macOS, Android, and iOS. However, notably, Surfshark's Linux client does not currently have a kill switch, which is something to keep in mind for Linux users.
 ExpressVPN: ExpressVPN calls its kill switch "Network Lock." It is a system-level kill switch that is enabled by default on desktop apps and even works on their router firmware. ExpressVPN's implementation is highly regarded - it loads on startup and applies to all device traffic, and it's designed to work seamlessly with their Lightway protocol for quick reconnections. On Android and iOS, ExpressVPN integrates with the OS-level features to block non-VPN traffic, providing a mobile kill switch as well.
ExpressVPN: ExpressVPN calls its kill switch "Network Lock." It is a system-level kill switch that is enabled by default on desktop apps and even works on their router firmware. ExpressVPN's implementation is highly regarded - it loads on startup and applies to all device traffic, and it's designed to work seamlessly with their Lightway protocol for quick reconnections. On Android and iOS, ExpressVPN integrates with the OS-level features to block non-VPN traffic, providing a mobile kill switch as well.
Mullvad: Mullvad VPN's philosophy is "always-on" privacy, so its client has an always-active kill switch by default. There's no toggle to turn the basic kill switch off - it's inherently always protecting you whenever the VPN is connected or trying to connect. Mullvad also offers a "Lockdown mode" (as mentioned earlier) that goes a step further by preventing any internet access when the VPN is off or the app is closed. This is essentially the persistent kill switch concept.
 Proton VPN: Proton VPN includes a kill switch in its applications (called Permanent Kill Switch in settings). Proton VPN's kill switch can run in a mode where it stays active even when you disconnect manually, similar to Mullvad's approach, thereby forcing all traffic through the VPN at all times for maximum safety. Proton also supports always-on VPN on Android, etc. (Proton's documentation confirms that their kill switch will block all network communications if the VPN drops, and they also have an "Always-On VPN" setting for persistence).
Proton VPN: Proton VPN includes a kill switch in its applications (called Permanent Kill Switch in settings). Proton VPN's kill switch can run in a mode where it stays active even when you disconnect manually, similar to Mullvad's approach, thereby forcing all traffic through the VPN at all times for maximum safety. Proton also supports always-on VPN on Android, etc. (Proton's documentation confirms that their kill switch will block all network communications if the VPN drops, and they also have an "Always-On VPN" setting for persistence).
Others: Most well-known paid VPNs like Private Internet Access (PIA), CyberGhost, IPVanish, VyprVPN, etc., have introduced kill switch features. Implementation quality varies - for instance, some might require you to turn it on in settings (it might be off by default), and not all providers extend the kill switch to all their platforms. Free VPN services are less likely to offer a kill switch due to the added complexity and cost of implementation (and if privacy is critical, free services often have other risks). Always check the documentation: a good VPN provider will explicitly mention if they have a kill switch and on which devices it's supported.
Usage Tips and Potential Drawbacks
Using a VPN kill switch is straightforward, but here are a few tips and things to be aware of:
Enable it when privacy matters: It's wise to keep the kill switch on whenever you're doing anything sensitive or when using untrusted networks. Many VPN apps have a simple checkbox or toggle in their settings to enable the kill switch (often labeled "Internet Kill Switch" or similar). On mobile, you might need to enable the system's always-on VPN feature as well for maximum protection.
Be prepared for disruptions: Remember that if the kill switch activates, you will lose internet access for a short time. If you're in the middle of a live activity (video call, online game, etc.), it will get cut off. The connection will resume once the VPN reconnects, or you may have to manually reconnect the VPN. This can be annoying, but it's the intended behavior to keep you safe. If you notice frequent VPN drops causing interruptions, you might want to troubleshoot your network or switch to a more stable VPN server/protocol (e.g., some protocols like OpenVPN UDP can be less stable than TCP in certain networks).
Captive portals and networks: Sometimes, a kill switch can interfere with things like captive portals (the Wi-Fi login pages at airports or hotels). For example, if you connect to a new Wi-Fi that requires a web login, a persistent kill switch might block the login page from loading because it's trying to go around the VPN. In such cases, you may need to temporarily disable the kill switch or the VPN, sign in to the Wi-Fi, then reconnect the VPN. Some VPNs have smart features to handle this, but if not, just be aware of this behavior.
Test your kill switch: It's a good idea to test that the kill switch works as advertised. You can do this by connecting the VPN, then disconnecting your VPN in an unsafe manner (e.g., force-quit the VPN app or disconnect it and see if your internet stops). There are online tools to check if your IP is leaking. A proper kill switch will cut your connection so effectively that you shouldn't be able to load any webpage until the VPN is back on. If you find that you can still browse the web with the VPN off (and kill switch on), then something is wrong - either the kill switch isn't functioning on your device or there's a misconfiguration.
When might you turn it off? Generally, you want the kill switch on whenever privacy is a concern. But there are a few scenarios where you might temporarily disable it: for example, if you're on a trusted network and need to access something that doesn't work with VPN, or if the VPN server is unstable and you prefer a moment of connectivity over continuous drop/reconnect cycles. Just remember to turn it back on when you're done. Some advanced users might disable the kill switch for specific tasks like LAN gaming (where a brief IP exposure isn't critical), but in normal use, leaving it on is the safest choice.
Conclusion
A VPN kill switch is an essential feature for anyone serious about maintaining online privacy and security. It acts as your digital seatbelt, ensuring that even when your VPN encounters bumps (or breaks down entirely), your identity and data remain secure. By automatically cutting off internet access during VPN dropouts, the kill switch safeguards you from accidental leaks — whether you're guarding against snoopers on public Wi-Fi, avoiding punitive actions for torrenting, or bypassing government censorship.
When evaluating VPN services, always consider the kill switch: how it's implemented, whether it's system-wide or app-specific, and if it fits your needs. The right kill switch setup will give you confidence that you're never exposed online, even for a moment. In a time where a single IP address reveal can compromise your privacy or safety, this feature provides invaluable peace of mind. Keep it enabled, pair it with a trustworthy VPN provider, and you can rest assured that if anything goes wrong with your VPN connection, the kill switch has got you covered - instantly and silently.
Stay safe, and happy (secure) browsing!

 Felix Bauer is an IT security consultant and tech writer with a passion for all things cybersecurity, privacy, and open source. For more than 20 years, he’s been helping people and businesses protect their digital lives, with a special focus on antivirus protection for everyday users.
Felix Bauer is an IT security consultant and tech writer with a passion for all things cybersecurity, privacy, and open source. For more than 20 years, he’s been helping people and businesses protect their digital lives, with a special focus on antivirus protection for everyday users.